
Could a single compromised password bring your restaurant’s transaction processing to a halt during Saturday night service?
It happened to nearly 300 restaurants in January 2023 when a ransomware attack forced Yum! Brands to close KFC, Pizza Hut, and Taco Bell locations for an entire day. Your POS terminals process hundreds of card payments during peak hours. Each transaction creates an opportunity for attackers targeting payment data.
43% of businesses identified cyber security breaches in the last 12 months. About 80% of restaurant transactions are now digital, meaning more customer payment data flows through POS infrastructure than ever before.
The consequences go far beyond operational disruption. Breach-related downtime during peak service creates immediate revenue loss. Customer trust evaporates when payment card data is compromised. And restaurants operating on thin margins can’t absorb regulatory penalties, forensic costs, and customer compensation.
Five Critical Controls That Protect Restaurant POS Systems
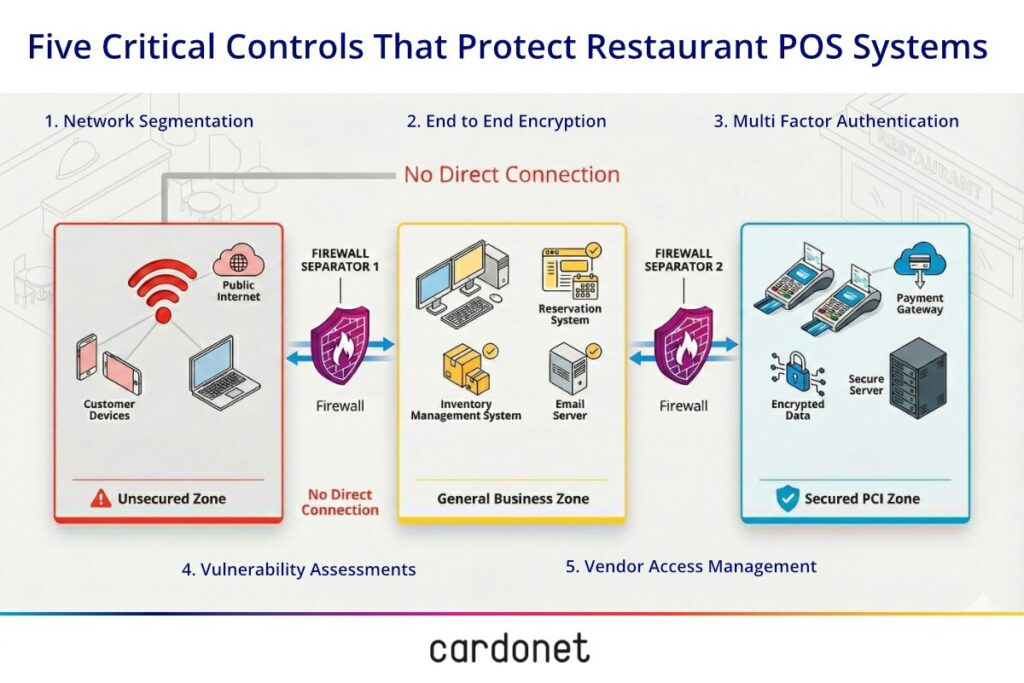
POS security isn’t about buying the latest product.
It’s about implementing layered controls that work together to protect your payment infrastructure. I’ve implemented these architectures across multi-site restaurant groups – they address the attack patterns that compromise restaurants while functioning reliably during your busiest service periods.
1. Network segmentation isolates your POS terminals from other restaurant systems.
Your guest Wi-Fi, back-office computers, and kitchen displays can’t be used as steppingstones to reach payment systems. When attackers compromise one part of your network, they’re contained there.
Think of network segmentation as building walls inside your network:
- Payment systems sit behind firewalls restricting system communication
- Guest Wi-Fi operates on a separate segment
- Back-office computers can’t directly access POS terminals
- Kitchen displays and reservation systems stay isolated from payment processing
One restaurant discovered this protection’s value when an employee clicked a phishing link on a back-office computer. Because their POS systems sat on a separate network segment, the attacker couldn’t pivot to payment terminals.
2. End-to-end encryption protects card data from the moment it enters the reader.
Point-to-point encryption (P2PE) encrypts payment information before it reaches terminal memory, where malware typically operates. PCI DSS mandates that card data is encrypted from the point of interaction and only decrypted in secure processing environments.
This creates minimal windows where malware can attempt capture.
But encryption alone isn’t enough – you need secure key management, regular cryptographic updates, and monitoring to verify encryption remains active. The encryption architecture must function automatically without requiring staff intervention during busy service periods.
3. Multi-factor authentication prevents unauthorized access even when passwords are compromised.
Phishing attacks remain the most prevalent breach vector, experienced by 85% of businesses that identified a breach. MFA adds a second verification step that attackers can’t bypass with stolen credentials alone.
This becomes critical when compromised vendor credentials frequently provide attackers with their initial access point. Requiring MFA for all remote access means stolen passwords alone won’t grant attackers entry to your payment systems.
4. Regular vulnerability assessments identify security gaps before criminals exploit them.
Your internet-facing systems need systematic testing:
- Online ordering platforms
- Remote access portals
- Payment gateways
- Mobile app integrations
Most businesses have implemented basic technical controls – malware protection (77%), password policies (73%), network firewalls (72%), and cloud backups (71%). But implementation without regular validation creates false confidence.
Vulnerability assessments systematically identify where configurations have drifted and where new vulnerabilities have emerged.
5. Vendor access management controls who can reach your payment systems remotely.
Criminal cyberattacks often result from compromised service provider credentials, allowing access and the ability to deploy malware across multiple locations. Every third-party vendor with remote access represents a potential attack vector.
Key vendor management controls:
- Restrict access to minimum necessary systems
- Require MFA for all remote access
- Log all vendor activities
- Review logs regularly for anomalous patterns
- Establish security requirements in contracts
These five controls form the foundation of restaurant POS security architecture. They work during busy service periods without slowing transaction processing and protect against attack patterns that actually compromise restaurants while meeting core PCI-DSS compliance requirements.
How POS Breaches Actually Occur
The attack mechanics are straightforward: card data exists briefly in unencrypted form in terminal RAM during payment processing. POS malware scans this RAM window, capturing data before encryption.
Attackers typically acquire initial access through compromised remote support credentials.
Third-party vendors maintain persistent access for legitimate support purposes. This supply chain attack vector proves particularly effective because vendors often have elevated privileges and access multiple restaurant locations.
Every vendor security assessment I conduct reveals the same vulnerability pattern.
Major restaurant chains have experienced this:
- Wendy’s discovered compromised vendor credentials led to malware deployment across hundreds of locations
- NCR’s Aloha POS software was compromised by the BlackCat ransomware group in April 2023, affecting thousands of restaurants
The average time between initial compromise and discovery can extend nearly a year.
During this window, malware silently exfiltrates card data from every transaction processed. By the time detection occurs, thousands of customer payment cards may be compromised. This extended dwell time explains why breach notification letters often reference incidents from months earlier.
Common attack vectors include:
- Compromised vendor remote access credentials
- Phishing attacks targeting restaurant staff
- Unpatched vulnerabilities in POS software
- Weak or default passwords
Network architecture failures compound these vulnerabilities. POS terminals sharing network segments with guest Wi-Fi or back-office systems create lateral movement opportunities. An attacker who compromises your guest Wi-Fi can pivot to payment systems if proper segmentation doesn’t exist.
Securing Operations During Peak Service
Security architectures must function reliably during peak transaction volumes without creating operational friction.
Your POS system processes hundreds of cards during weekend dinner service. Security controls that impede transaction speed typically get disabled by staff attempting to maintain operational efficiency.
This undermines your entire security posture.
I’ve watched this pattern repeat across restaurants: perfectly implemented security controls that staff bypass because they slow Saturday night service. The same thing happens during Valentine’s Day rushes, Mother’s Day brunches, and New Year’s Eve. Staff prioritize getting customers served over following security protocols that create friction.
The solution isn’t accepting this tradeoff.
It’s implementing security that operates transparently:
- Network segmentation functions at infrastructure level – no staff intervention needed
- End-to-end encryption protects automatically regardless of transaction volume
- Monitoring distinguishes legitimate high-volume patterns from anomalous activity
- False positive alerts are minimized to prevent staff desensitization
Let’s quantify the operational risk. For an average restaurant doing $5,000 in card transactions during a typical Saturday dinner service, one hour of POS downtime represents direct revenue loss. That’s $5,000 you can’t recover – customers don’t return to pay for meals they ate hours ago. They leave, post negative reviews, and choose competitors next time.
A full day of downtime during peak season?
That’s business-threatening for restaurants operating on 3-5% profit margins. This is why the 300 restaurants affected by the Yum! Brands ransomware attack chose to close completely rather than attempt manual payment processing.
Effective operational security requires:
- Transparent controls that don’t slow transaction processing
- Monitoring tuned to normal service-period volumes
- Clear escalation procedures for security events during service
- Backup payment processing methods if systems go offline
- Decision frameworks defining who authorizes taking POS systems offline
Internal reporting to senior management remains the most common action following a breach, with 76% of businesses informing directors. But your plans must address whether to continue processing transactions during active incidents and how to switch to manual card imprinters if necessary.
The question isn’t whether to implement security. It’s whether your security architecture accommodates operational reality.
Delivery Platforms and Third-Party Integration Risks
Online ordering and delivery platform integrations create additional attack surface beyond your restaurant-controlled infrastructure.
These systems often require direct connections to your POS, inventory management, and customer databases. The integration credentials and API access represent high-value targets for attackers. When delivery platforms are compromised, attackers can potentially pivot to every connected restaurant.
Just over one in ten businesses reviewed cyber security risks posed by their immediate suppliers, with under one in ten looking at their wider supply chain. This represents a significant security gap.
Apply the same vendor access management framework from Control #5 to your delivery and ordering integrations: restrict access to minimum necessary systems, require MFA for all connections, log activities, and establish security requirements in contracts before integration.
Compliance: Meeting PCI DSS Requirements
PCI DSS creates baseline security requirements globally. Payment processors enforce these through monthly penalties escalating from $5,000 to $100,000, with potential merchant account termination for persistent non-compliance.
If you process 800,000 transactions annually, you’re Level 4 compliance. This requires annual self-assessment questionnaires, quarterly network scans by approved vendors, and attestation of compliance forms. The five controls outlined in this article directly address PCI DSS requirements 1, 2, 3, 4, 7, 8, and 10.
Data protection regulations add jurisdiction-specific risk. Organizations face penalties under UK GDPR (up to £17.5 million or 4% of turnover) and US state breach notification laws. Technical security failures trigger both PCI violations and data protection breaches simultaneously, compounding financial exposure.
But the real cost isn’t the regulatory fine. It’s the operational impact – downtime, customer notification expenses, forensic costs, and reputation damage compound far beyond the initial penalty.
Why This Matters for Restaurants
POS security directly protects restaurant revenue streams by maintaining continuous payment processing capability.
Revenue continuity comes first.
Breach-related downtime during Saturday evening service or holiday periods creates immediate revenue loss that restaurants operating on thin profit margins can’t absorb. Your customers have numerous dining options. They’ll choose competitors when they can’t pay with their preferred method.
One hour of POS downtime during peak service can represent thousands in lost revenue. A full day – like the 300 restaurants that closed due to ransomware – compounds this exponentially.
That’s not recoverable revenue. It’s gone.
Customer trust is an intangible asset that breaches destroy rapidly.
Restaurants depend on repeat customers and positive local reputation. Both suffer lasting damage when payment card data is compromised. Your regulars won’t come back if they’re concerned about card security. New customers will choose competitors with better security reputations.
The restaurant industry operates on thin margins, and breaches create existential threats.
Consider a single-location restaurant with $2M annual revenue operating at 4% margins. Your annual profit is $80K. One major breach with forensic costs ($50K), customer notifications ($20K), and lost revenue during investigation ($30K) wipes out 125% of your annual profit. Add regulatory penalties, and you’re looking at multiple years of profit gone.
Costs for restaurant breaches are rising and lead to reputational damage, operational disruptions, loss of customer trust and legal penalties. You can’t afford the financial strain from preventable security breaches when the combined weight of all these costs threatens your continued operation.
Protecting Your Restaurant: Next Steps
Understanding POS security threats is the first step. Implementing protection requires expertise.
Your payment infrastructure needs professional security assessment. The five critical controls – network segmentation, end-to-end encryption, multi-factor authentication, vulnerability assessments, and vendor access management – require proper implementation to function effectively during busy service periods.
Cardonet specializes in restaurant IT security and PCI-DSS compliance for hospitality businesses. Our team understands the unique challenges restaurants face: tight budgets, extended operating hours, high staff turnover, and the need for security that doesn’t disrupt service.
Do a POS security assessment to identify vulnerabilities in your payment infrastructure before attackers do.
We’ll evaluate your current controls, assess PCI-DSS compliance gaps, and provide a clear roadmap for protecting your restaurant. Contact Cardonet today to secure your POS systems and protect your customers’ payment data.
Summary
Restaurant POS security starts with five critical controls: network segmentation, end-to-end encryption, multi-factor authentication, regular vulnerability assessments, and vendor access management.
These controls form a defense in depth architecture protecting against the specific attack patterns that compromise restaurant payment systems. The threat landscape intensified, with 43% of businesses experiencing cyber breaches. Restaurants are vulnerable due to extended operating hours, high staff turnover, thin profit margins, and complex technology ecosystems.
PCI-DSS compliance represents mandatory baseline security with serious financial consequences. Payment card network fines range from $5,000 to $100,000 monthly with potential merchant account termination. But the real cost comes from operational disruption, customer trust erosion, and revenue loss during peak service periods.
Effective POS security protects restaurant revenue continuity, customer trust, and operational resilience – business-critical outcomes that justify security investment as operational necessity.
FAQs: Restaurant POS Security
What are the five most important POS security controls for restaurants?
Network segmentation isolating payment systems, end-to-end encryption protecting card data, multi-factor authentication preventing unauthorized access, regular vulnerability assessments identifying security gaps, and vendor access management controlling third-party remote access. These controls address primary attack vectors while functioning reliably during busy service periods.
What are the financial consequences of PCI-DSS non-compliance?
Payment card network penalties range from $5,000 to $100,000 monthly with potential merchant account termination. Data protection fines can reach £17.5 million or 4% of global annual turnover. Major hospitality breaches have triggered eight-figure penalties like the £20 million British Airways fine.
How long can POS malware steal customer data before detection?
POS malware can silently steal card data for months by scanning terminal memory for unencrypted payment data during transaction processing. The average time between initial compromise and discovery can extend nearly a year. Regular security monitoring significantly reduces this window.
Should restaurants with delivery platform integrations have additional security concerns?
Yes. Delivery platform and online ordering integrations require direct connections to your POS and customer databases, significantly expanding your attack surface. Just over one in ten businesses reviewed cyber security risks posed by their immediate suppliers. Apply the same vendor access management framework to all third-party integrations.
What security measures work during busy service periods without slowing transactions?
Network segmentation and end-to-end encryption operate transparently without requiring staff intervention or slowing transaction processing. These architectural controls function at the infrastructure level, protecting payment data automatically. Properly configured monitoring systems distinguish legitimate high-volume patterns from anomalous activity.



You must be logged in to post a comment.